Cyril Gy
Pérennisons votre transformation digitale
Applications mobiles natives iOS (iPhone, iPad, watchOS, tvOS), applications backend (Go, Docker) ou sites internet responsive (vitrine, e-commerce), j'apporte plus de dix ans d'expertise pour vos projets numériques.
À Propos
Humain avant tout
Je m'appelle Cyril et je serais heureux de vous accompagner dans le développement de vos projets numériques.
Il est important de garder en mémoire que l'humain est la base de tout projet et je serai le garant de cet esprit.
Responsabilisation
Lors de mes précédentes expériences, j'ai eu la preuve que la confiance, le respect, l'écoute et l'humilité sont le ciment de la réussite de tout projet.
La responsabilisation et la transparence sont indispensables pour motiver, impliquer et libérer chaque membre de votre équipe pour mener à bien les projets.
Développeur Senior OVHcloud
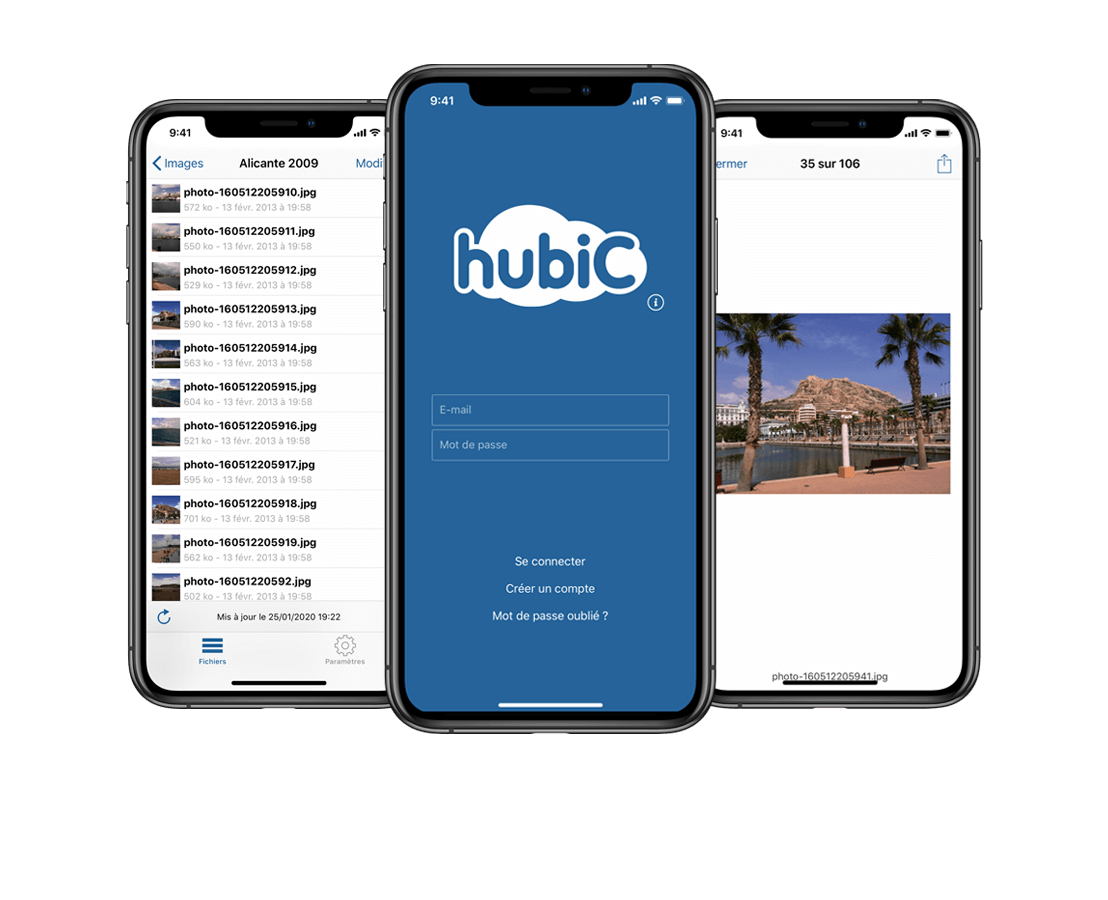
Arrivé en 2010 chez OVHcloud, j'ai participé activement à la mise en place du pôle mobile avec l'équipe dirigeante. Durant plus de huit années et dans un contexte international, j'ai géré des projets ambitieux tels que MoMi iOS, hubiC iOS et macOS (Objective-C, Swift, Xamarin), des SDK ou encore des projets expérimentaux (VoIP, montres connectées, TV). J'ai travaillé de concert avec les équipes projet, UX/UI, QA et traducteurs afin d'assurer la mise en ligne des différentes versions.
Développeur Web Akena
Pendant dix-huit mois j'ai approfondi mes compétences en développement web (front et backend), bases de données, administration des systèmes et serveurs Linux et SEO.
Télécharger mon CVMaster 2 Informatique
Dipômé en 2008 d'un Master 2 Professionnel en Technologies Nouvelles des Systèmes de l'Information et Décisionnels à l'université de Valenciennes, j'ai solidifié mes acquis en ingénierie et développement informatique lors de stages de longue durée dans des start-ups innovantes.
Certification Entrepreneuriat
Certifié en 2019 par la formation Construire et conduire un projet entrepreneurial de la BGE Hauts-de-France, j'ai de robustes connaissances en étude de marché, gestion financière, communication et marketing pour conduire à bien des projets d'envergure.
Télécharger mon CVServices
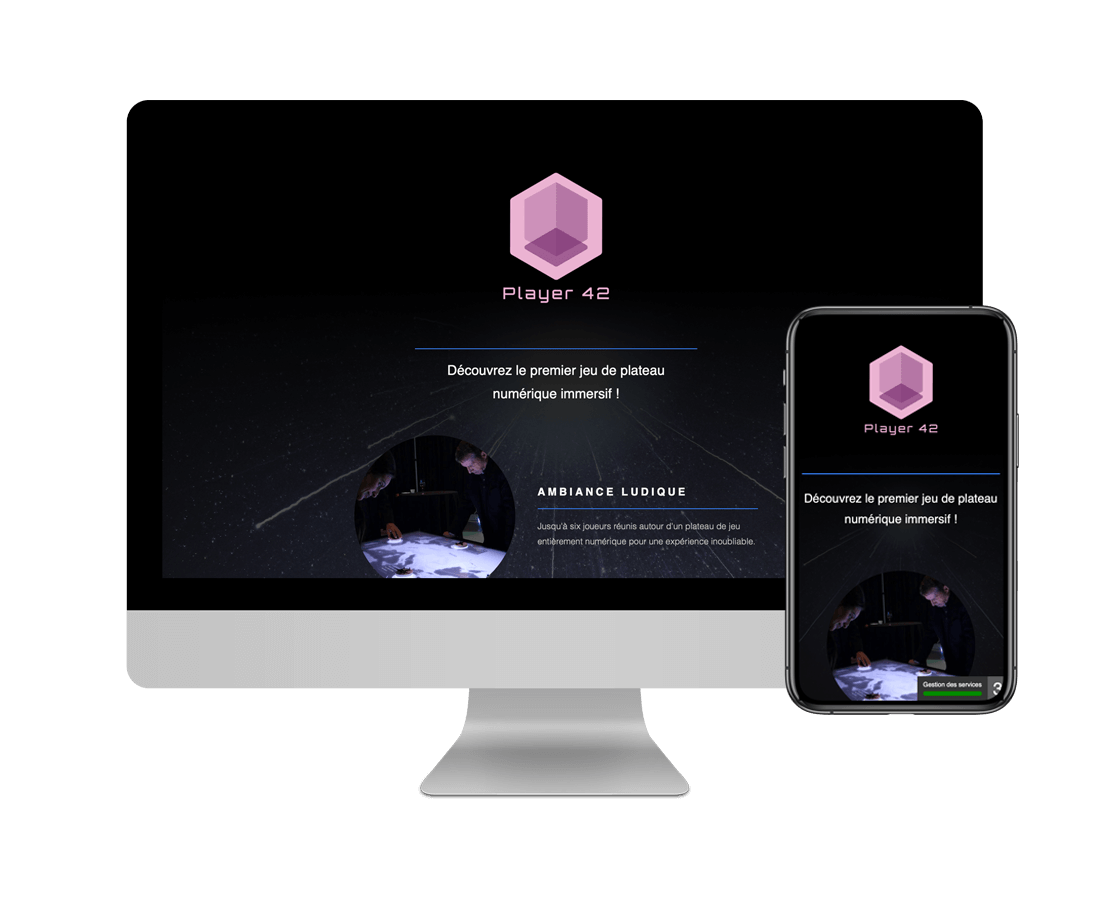
Applications mobiles iOS
Développement et/ou mise à jour d'applications mobiles natives iOS, WatchOS et tvOS. Support des deux dernières versions majeures d'iOS. Langages Swift & Objective-C.
Lead Tech iOS
Management d'une équipe de développeurs sur des projets mobiles natifs iOS (jusqu'à quatre développeurs). Architecture logicielle. Langages Swift & Objective-C.
Demander un devisApplications front-end
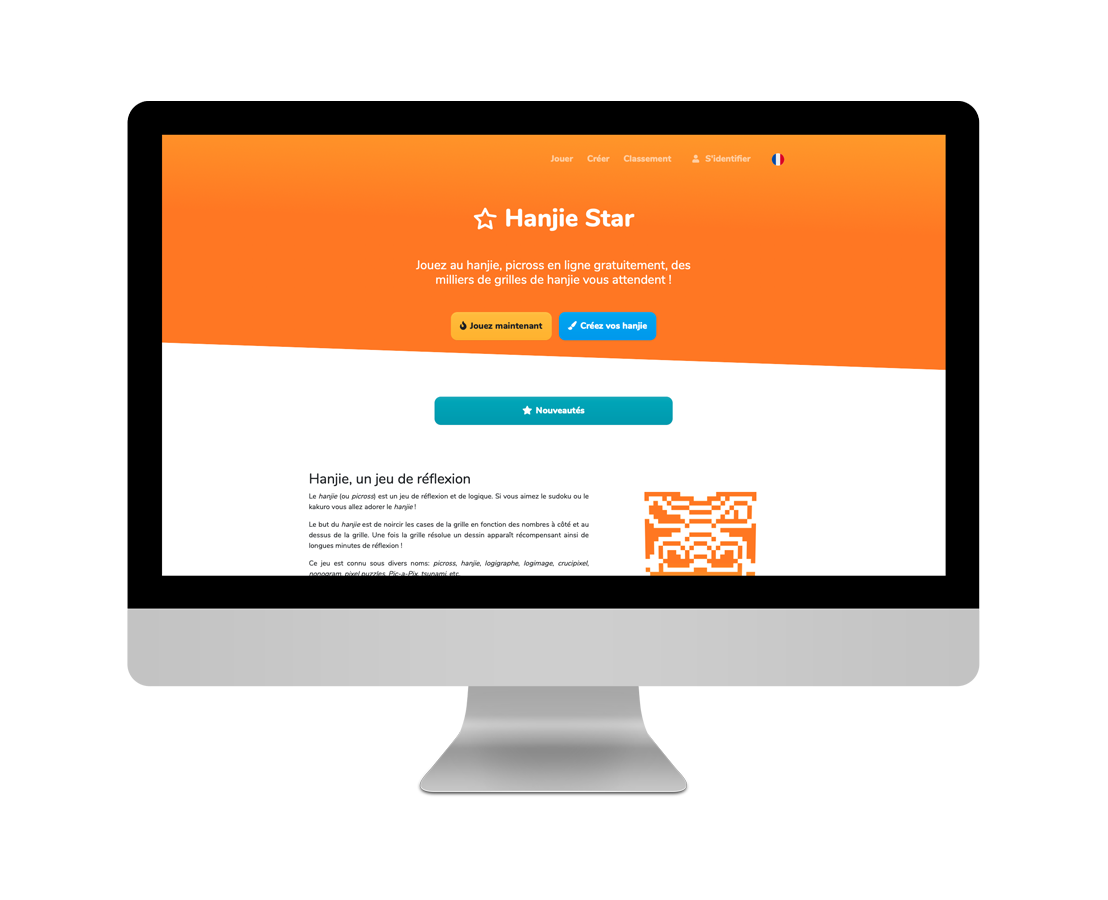
Développement et/ou mise à jour de pages web et de fonctionnalités interactives. Je m'adapte rapidement et aisément à tout framework front-end. Langages Javascript, HTML, CSS.
Sites vitrines ou e-commerce
Mise en place d'un site vitrine statique ou e-commerce dynamique : code, icones libres de droit et gratuites, hébergement, nom de domaine. Textes et photos non-compris.
Demander un devisApplications back-end
Développement et/ou mise à jour d'applications back-end. Je m'adapte rapidement et aisément à tout framework back-end et outil de déploiement. Langage GO. Bases de données MongoDB, MySQL. Déploiement Docker & Ansible.
Demander un devisChief Technical Officer
Vous démarrez un nouveau projet numérique et vous désirez vous faire accompagner pour mettre en place rapidement et sereinement votre infrastructure et vos applications front-end, back-end et/ou mobiles.
Projet innovation
Mise en place de processus d'innovation centrés autour des clients et de votre équipe projet. Méthodologies Lean Start-up, Innovator's method.
Demander un devisContact
Pour toute information complémentaire ou demande de devis pour votre projet numérique, vous pouvez me contacter par e-mail, par téléphone ou via un média social. Je vous répondrai rapidement !
Cygy Solutions
SASU au capital de 500,00 €
R.C.S. Valenciennes 885097220
Code APE 7022Z
N° TVA : FR92885097220
Siège social : 5 rue des Lilas - 59860 Bruay Sur l'Escaut - France
Directeur de la publication : Cyril GY
Président : Cyril GY